Learn How to Verify PCIe Integrity and Data Encryption (IDE) Security Logic at the 2022 PCI SIG Developer Conference

Making sure that digital logic enables secure data to safely flow through a system is a critical task for RTL functional verification (1, 2). Thus, for anyone employing PCIe Gen5 or Gen6 in their designs, verification of the Integrity and Data Encryption (IDE) Security subsystem is essential. As shown on the left two columns of Figure 1 below, without the real-time encryption provided by IDE, hackers could modify the data transiting your PCIe bus – something that would be difficult, if not impossible to detect. But as illustrated on the right-hand-side, the IDE standard’s addition of a Message Authentication Code (MAC) schema makes it easy to detect any tampering.
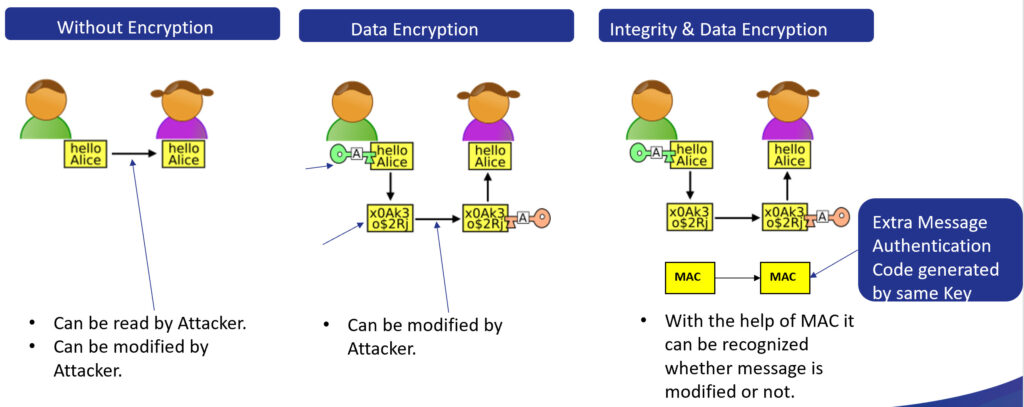
Figure 1: The need for Integrity and Data Encryption (IDE) Security
As important as IDE is to the whole system, adding this new hardware threatens to add even more schedule and cost to an already complex D&V flow. Fortunately, there are verification methodologies and Verification IP solutions that are relatively easy to adopt – enabling you to focus on to the differentiated parts of your product. Specifically, at the upcoming PCI SIG Developer Conference this June 21-22 at the Santa Clara Convention Center, members of the Questa Verification IP R&D team will explain what you need to know about verifying the RTL design of your IDE logic in the following presentations:
- IDE Verification and its Challenges
Richa Gupta
This presentation addresses a broad scope of IDE verification: it covers how to verify Aggregation, TLP Ordering, K-bit Toggling, Selective IDE; and the related issues of accounting for flow control credit, and properly verifying Selective IDE and Link IDE Streams on single TCs. - Implementing AES-GCM for PCIe IDE
Tufail Ansari and Gyana Khuntia
This will be a deep dive on the design and verification of AES Galois/Counter Mode (GCM) IP that generates and decrypts the MACs (referred to in Figure 1 above) – whether the implementation is sequential or parallel.
The presentations are virtually back-to-back after the break in Wednesday morning’s “(3) Members Implementation” track, so you can immerse yourself in the topic. To setup a meeting with our presenters and our other experts at the show – and to learn more about our other PCIe domain offerings in general – here is where you can contact us and register for the event.
Hope to see you there!
Joe Hupcey III,
for the Questa Verification Team
P.S. For completeness sake: IDE is also part of the Compute Express Link (CXL) protocol; and thus the techniques in the cited papers apply to IDE implementations in CXL designs as well.
Reference Links
1 – How Formal Techniques Can Keep Hackers from Driving You into a Ditch, Part 1 of 2
2 – How Formal Techniques Can Keep Hackers from Driving You into a Ditch, Part 2 of 2
3 – The PCI SIG 2022 Developers conference home page
4 – More information on how to contact us and register for the event